Online Business Systems
We are a Trusted Healthcare Security Partner.
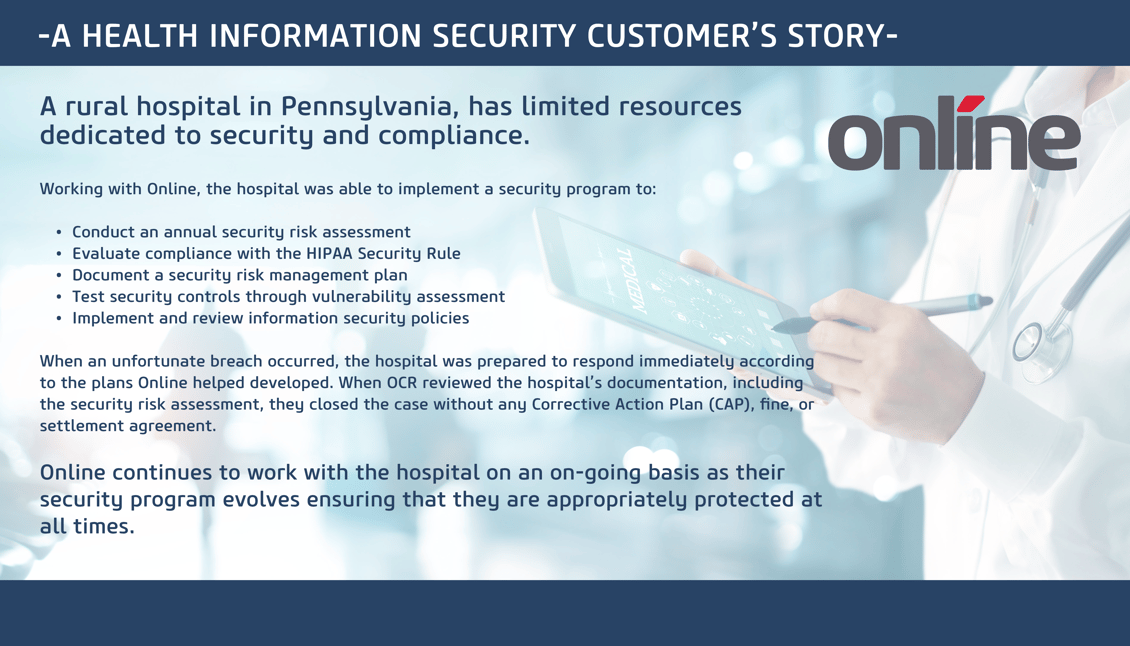
As you're already aware, hospitals find themselves under a lot of pressure to operate securely. Regulations such as HIPAA require trusted security programs be in place and continually updated, especially because the risk of a breach has never been higher.
Organizations that hire vCISOs report savings of up to 80% when compared to a full-time CISO role.

 Breach Protection for Client Data
Breach Protection for Client Data
The average cost to an organization that suffers a security breach is $7m. An Online vCISO safeguards your Protected Health Information by participating in strategy meetings and developing policies and key security management processes- all with an eye towards communication, mentorship, and reducing the risk of breaches associated with penalties and fines.
 Cost-Effective Security Partner
Cost-Effective Security Partner
Organizations that hire vCISOs report savings of up to 80% in comparison to a full-time CISO. Online's vCISO service is backed by an entire team of top-tier security professionals. Intelligent, advanced, and measurable improvement to security posture become a reality for small-to-medium sized healthcare organizations like yours.

LEE BUTTKE
|

ROB HARVEY
|
|
Lee Buttke is a Director with Online Business Systems and |
As a Director of Online's Risk, Security and Privacy practice, Rob brings business and technology expertise from over twenty-five years in Information Technology. Rob specializes in his advisory services to healthcare companies working to address complex technology |
|
Request a video conference for YOUR initial scope assessment: |
Can YOU Afford to Take Chances With Your
Patients' Valuable Data?
Healthcare information breaches continue to rise, with the average patient record selling for 10x more than credit card info on the black market.
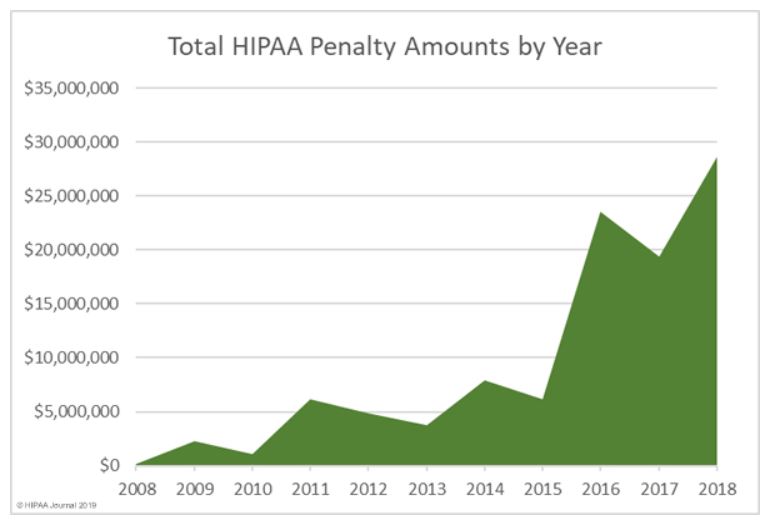
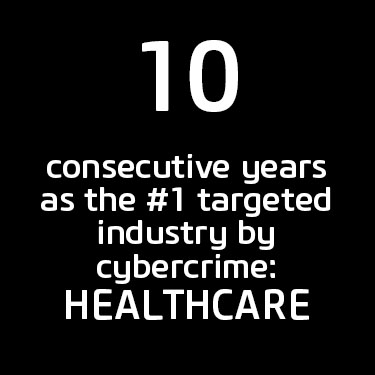
Healthcare Infosecurity Numbers to Consider:


What can a vCISO From Online
do for Your Healthcare Organization?
Governance
Online's experienced vCISO can establish an information security strategy and business alignment, create a security steering committee and develop an information security project charter.
Security Operations
A vCISO from Online will work with you to build out effective and all-encompassing capabilities to reduce and mitigate threats.
Risk Assessment
You can depend on our vCISO to assess and facilitate treatment of identified risks through enterprise management and audit committee using a risk register.
Compliance & Audits
Reduce the stress of audits with a vCISO from Online, to help you manage and facilitate readiness for external audits
(PCI, SOC2, HIPAA), track remediation of audit findings, and assist you with completing tedious third-party security questionnaires.
Risk Management
The risk of breach attempts on your patient data is inevitable, but our best practices and expertise will assess and facilitate remediation of those identified risks through enterprise management, and provide you with an audit committee using a risk register.
Security Architecture
Online's Risk, Security & Privacy team will oversee and make recommendations on your network segmentation, provide remote access controls, and establish cloud architecture security assessments.
Interested in hearing more about our vCISO solutions?
Read some thought leadership generated by Online's team of security subject matter experts: