
Jeff Man
Jeff Man, is an Information Security advocate, InfoSec Curmudgeon, PCI QSA; Trusted Advisor and speaker with over 40 years of experience in cryptography, risk management, information security and penetration testing. As a National Security Agency cryptanalyst, Jeff invented the "whiz" wheel, a cryptologic cipher wheel used by US Special Forces as well as the first software-based cryptosystem produced by the NSA and pioneered the agency’s first “red team”. Jeff actively shares his unique and valuable knowledge as an international speaker, author contributor to Tribe of Hackers and podcast host for Paul’s Security Weekly. He gives back to the industry through sitting on advisory boards as well as inspiring youth through diversity, equity and inclusion initiatives and mentorship. Jeff remains a driving force in the industry, bringing his deep expertise and no-nonsense approach to his role as a PCI QSA and Trusted Advisor at Online Business Systems.
 In early 2017, HP invited a group of cybersecurity industry bloggers and podcasters to gather for an HP Print Security “Tech Day” at their headquarters in Palo Alto, CA. The purpose of the gathering was to introduce the group to HP’s printer security program (#reinventsecurity), foster discussion, and get feedback on the program. This event was the precursor to a major marketing campaign for HP to promote everything they’ve been doing in terms of making their printers more secure and also building printers with “cyber resilience”, meaning they have the capacity to detect malicious or accidental actions and even recover from the attacks. HP has worked diligently to improve the security of printers which in turn helps to create a more secure enterprise network.
In early 2017, HP invited a group of cybersecurity industry bloggers and podcasters to gather for an HP Print Security “Tech Day” at their headquarters in Palo Alto, CA. The purpose of the gathering was to introduce the group to HP’s printer security program (#reinventsecurity), foster discussion, and get feedback on the program. This event was the precursor to a major marketing campaign for HP to promote everything they’ve been doing in terms of making their printers more secure and also building printers with “cyber resilience”, meaning they have the capacity to detect malicious or accidental actions and even recover from the attacks. HP has worked diligently to improve the security of printers which in turn helps to create a more secure enterprise network.
The Tech Day discussions included industry bloggers and podcasters covering many topics, and HP was very receptive to both positive and critical feedback. Topics included the technical aspects of enterprise printer security features, the expectations that HP has to produce a secure product, the need for increased user awareness to assure that printers are implemented and maintained securely, and the many ways that printers can be exploited for direct compromise of data (e.g. print jobs) but also that they can be leveraged as an attack platform or pivot point to gain access to the rest of the network. One particular topic of discussion was how to maintain the security of devices such as printers given the continuous “discovery” of vulnerabilities and weaknesses to systems and applications.
Somewhere during these conversations, the idea of HP starting a bug bounty program apparently took hold. To that end, HP announced just before Black Hat 2018 that it had entered a partnership with Bugcrowd to pay up to a $10,000 bug bounty to security researchers for the discovery of vulnerabilities in their printers. In short, HP is paying hackers to break into their devices.
HP invited me to Black Hat this year to continue discussions with them about their printer security efforts, particularly the new bug bounty program. They asked me to meet with several of their security experts, check out their latest marketing campaign featuring “The Fixer” (more on that later), ask questions, and provide feedback. 
The launch of the bug bounty program was one of the key highlights from Black Hat as this is the first time a bug bounty program has been launched specifically focusing on printers. The buzz actually started before the conference as HP went public with the program prior to the conference. The HP folks I talked to at during the week were very encouraged by the public response and direct feedback they were receiving during the week.
What is a bug bounty?
The idea of a bug bounty is to pay independent developers and security researchers (a.k.a. hackers) to share vulnerabilities that they have found in applications and systems with the companies that produce them. It is essentially outsourcing the research & development function, or at least supplementing that function. This concept is sometimes referred to as crowdsourcing. Companies like Bugcrowd have created a business model around brokering the relationships between the companies offering the bounties and the research community.
The concept of “public de-bugging” is not new in this industry. I remember in the early days of the “World Wide Web” the first commercial browser, Netscape Navigator, offered bounties for the discovery and reporting of bugs in its software. The Netscape company rather boldly said something to the effect of, “we know we’re putting out buggy software, and we are willing to pay you for reporting the bugs”. To them it was more advantageous than relying on internal testing and more importantly it helped them get new software and features to the market more quickly.
This resonates with many because in the connected world in which we now live it is nearly impossible to build in-house expertise, no matter the number of security researchers hired, that can match the tens of thousands of practitioners and researchers all over the world. Bug bounty programs have become prevalent, and the demand for such programs has resulted in the emergence of companies that are focused on administering and brokering the programs for an increasing number of manufacturers and developers.
Why the focus on security?
HP traces its origins back to the very beginning of the technology era when the founders, Bill Hewlett and Dave Packard, produced oscilloscopes out of a rented garage. In fact, the “HP Garage” is credited as being the birthplace of what is now known as Silicon Valley. HP has always prided itself on producing the best products from electronic monitoring/tracking systems, calculators, desk top computers, and of course, printers.
Today the company still holds to the values and corporate culture that Bill & Dave nurtured and considers producing highly reliable and secure products as an integral part of preserving the legacy and reputation that was so carefully cultivated by the founders. In addition to the commitment to provide secure printers with secure settings and configurations, the company has developed features that enable the printers to be “self-checking’ and “self-healing” in order to minimize the impact of any attack that is launched against the printer itself.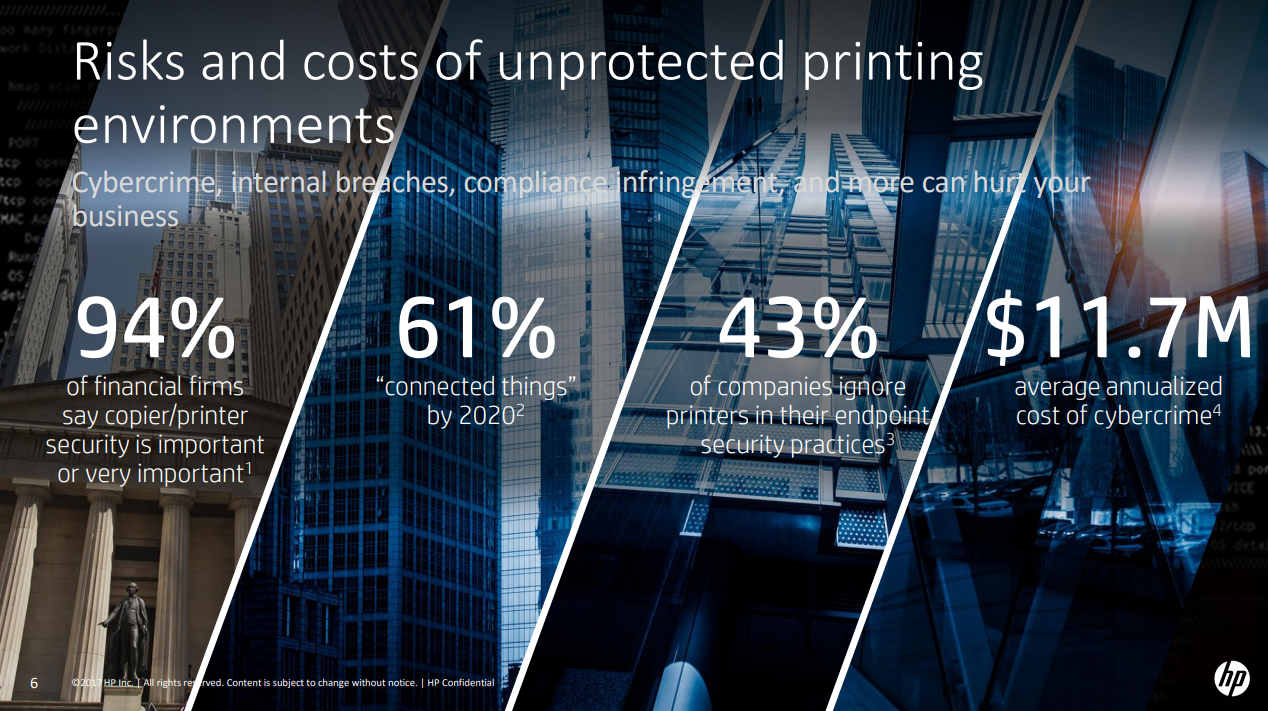
Implementation is key
HP has made a commitment to educate its customers on the threats that network printers pose to the enterprise and how to configure, maintain, and use printers in a secure manner. Not only can sensitive documents sent to the printer be intercepted or modified, the printers can give attackers a foothold into the corporate network. Numerous incidents of white-hat hackers taking over network printers have been reported, including an incident in 2017 where a hacker claimed to have accesses over 150,000 printers worldwide and force them to print a warning message to their owners recognizing the need to educate consumers on the risks that printers pose, HP has embarked on an extensive marketing campaign that revolves around educating consumers about the threat that networked printers pose through a series of dramatic short stories featuring a dubious character played by Christian Slater (Mr. Robot). The first episode is titled “The Wolf” and the second is titled, “The Wolf: The Hunt Continues”. The third installment in the series introduces a new and enigmatic character dubbed “The Fixer” played by the often villainous character actor, Jonathan Banks (Breaking Bad, Better Call Saul). To see the latest installment of the HP series and to learn more about printer security check out: “The Wolf: True Alpha”. #reinventsecurity
To learn more about Online's Risk, Security and Privacy practice check out our website.

.png)
Submit a Comment