The other day as I was working on a report for a client, I found myself writing “first things first” to describe why getting the inputs side of security monitoring operations or SecMonOps is critical to a successful deployment.
Unfamiliar with SecMonOps?
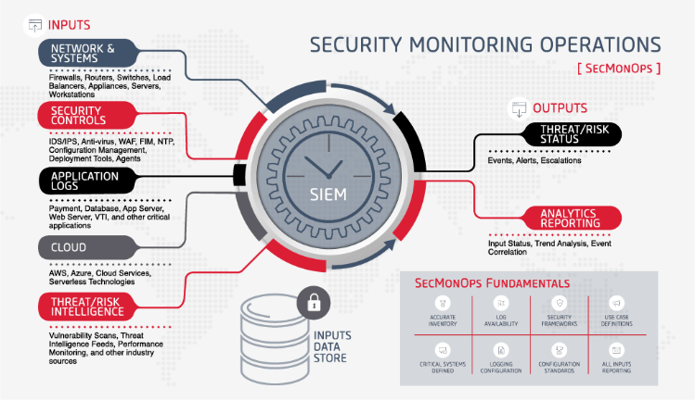
It is the governance and use of a SIEM tool (whether it is delivered on prem or through a MSSP) to collect logs from a systems (inputs), interrogate those logs for issues which require attention (SIEM), and alert your organization to the issue (outputs).
This graphic below illustrates the inputs, outputs, data storage and foundational elements of SecMonOps
That got me to thinking about what other axioms are applicable to SecMonOps.
The first four things I scrawled down were:
- First things first
- Begin with the end in mind
- Garbage in - garbage out
- Can’t see the forest through the trees
As I wrote them down I quickly realized that they are more than just common phrases, they are critical principals of a successful SecMonOps implementation. Far too often our RSP practice finds clients who have skipped right past one or more of these principles.
The result is a SecMonOps implementation that has gaps in coverage, is missing the mark in alerts, and is unable to detect vulnerabilities or bad actor fingerprints.
And so I paused writing my report, and started writing this blog:
| 1. | Begin with the end in mind – What are the goals and objectives you have set for your SIEM? The quality of implementation of your security monitoring operations is probably reflective of the time and resources you and your team have made to answering this question. Take the time to answer the question fully and make sure there is consensus on your team. Set up KPI’s to verify how well you are meeting these objectives! |
| 2. | First things first – It all starts with identifying the devices, security tools and applications being monitored. Fail here, and it won’t matter how money has been committed to SecMonOps or the quality of the SIEM Your SecMonOps will likely miss the very things it was implemented to catch. All critical devices, security controls, applications must be reporting to the SIEM. Answer the following questions to determine if your security monitoring operations are “first things first and be actionable by SecOps or ITOps”:
|
| 3. | Garbage in/Garbage out – No matter how effective the SIEM tool is or what methodology is used to interrogate logs, your SecMonOps implementation will be ineffective if the log data being pushed to the SIEM is not comprehensive (incomplete data in event logs), lacks depth (missing devices, security controls, critical applications not reporting to the SIEM), doesn’t have integrity (not capturing all needed events), and is is not properly tuned to reduce white noise. |
| 4. | Can’t see the forest through the trees – With the volume of alerts that can be generated by the SIEM, it can be tempting to focus on simply meeting internal Service Level Objectives (SLOs) for responding and resolving alerts (i.e., how fast alerts are acknowledged by the SOC, how quickly are the cases resolved, etc.). However, if your focus is too narrow you will miss out on valuable insights such as potential fingerprints of bad actors, new vulnerabilities, and overall SecMonOps performance. You may want to consider a couple of key questions.
|
Whether you are just starting to implement Security Monitoring Operations or you have been doing it for over a decade, these four axioms apply. It’s never too late to step back and re-evaluate the health of SecMonOps. Identifying and closing gaps you identify during this review will better position your organization to identify vulnerabilities and bad actors.
If you need assistance in implementing SecMonOps or would like an independent point of view of your SecMonOps, give us a call. Our RSP team can help you raise the bar in your SecMonOps. In the meantime, I have a report to finish!





Submit a Comment