Will Bechtel
** Republished from March 2020, with updates **
With many employees returning to the office this summer, attentive IT leaders are worried that employees may have picked up bad cybersecurity habits since working from home. (These very valid concerns are outlined here.) This is an ideal time for organizations to return to engaging with Red Team Testing and protected valuable assets from all forms of cyber threats.
Network attacks are on the increase, and hackers are being forced to become more and more sophisticated as we build even stronger defense strategies to shut them down.
Cybercriminals are Getting Smarter
The New York Times recently published some staggering stats for US organizations, reporting a 41% increase of compromised files in just one year, indicating an overwhelming surge of breaches. For a single month alone, the average payment demand was $190,946 with several organizations facing ransom demands in the millions of dollars. And these assailants are persistent, remaining virtually undetected as they patiently infiltrate organizations, sometimes with attacks spanning years.

The longest standing insider attack lasted 30 years inside the network of Boeing, with perpetrators mining information and planning their attack over the extended period, while Yahoo still holds the all-time record of 3 billion compromised records suffered during a two-year breach.
Even businesses that might think they don't have any valuable information to protect could be at risk of someone trying to take over the network, installing malware, disrupting services, and possibly creating more havoc.
All it takes is one weak entry point for a breach to occur, and what we have learned is that cybercriminals are determined to find it.
Exploiting Your Weaknesses:
Penetration Testing vs. Red Team Testing
Many organizations have mature security measures in place to deter phishing and malware attacks and detect unusual behavior. They may even conduct routine penetration tests to find as many vulnerabilities and configuration issues as possible, exploit them, and determine the risk they represent. Moreover, penetration testing has become a must for most industries and is required by law in health organizations (under HIPAA), financial institutions (for FDIC compliance), businesses accepting or processing payment cards (PCI DSS), and in critical infrastructure entities (NERC).
While most organizations understand the need to perform security penetration testing to ensure their environments are well protected against cyber threats, if not conducted properly, the results may lead many organizations to have a false sense of security.

The is due to the way most penetration tests are conducted. Most penetration tests executed today are set up to test specific targets in specific ways; thus, creating attack scenarios that are not as effective as a well thought out Red Team approach designed to account for changing threats.
For example, many organizations perform an annual external network penetration test and set several restrictions on that testing such as:
- Scope limits – including only systems or networks that are designated to be related to a given compliance objective.
- Time of day limits – testing must only be conducted during off-hours in order to avoid impacts to production environments or data processing time windows.
- Duration limits – strictly limiting the time for tests to be conducted into the shortest time-frame possible to achieve near-term deadlines.
To learn more about the six main types of penetration testing, check out this article from Kevin Mitnick.
While there are many good business decisions driving the constraints above, they can, in many cases, end up masking the risk posed by real-world threats that do not conform to these limitations. When done right, penetration testing is a proven strategy used to assess your network security and expose technology vulnerabilities. In fact, it's often used as a tactical measure in Red Team engagements; but a stand-alone network-focused penetration test does not factor in all of the hidden-in-plain-site weaknesses.
Enter the Red Team
The term Red Team comes from military origin where it was identified that to realistically test a defense, there was a need to have a thinking attacker that could change tactics as opposed to a predictable attacker that follows a predetermined script.
The Red Team represents the attacker in these scenarios, with the term Blue Team referred to as defenders. In cybersecurity, Red Teaming is usually a more comprehensive and realistic attack scenario than a traditional penetration test. Cybersecurity Red Teaming usually implies that many of the typical constraints that are placed on penetration testing are removed. Red Teams are typically given the flexibility to perform attacks using many different attack vectors and with fewer constraints than more traditional Penetration Tests.

Broadly, Red Teaming attacks are from the perspective of the bad guys to help your team gain visibility and understanding into how a real attacker would behave.
A typical Red Team engagement would have some or all of the following characteristics:
- Wide scope to exploit – an engagement may include network and wireless penetration testing, social engineering (phishing/Vishing), and physical site penetration testing.
- Few limits on the dates/times that an attack may be launched – if the Red Team determines the target organization is most vulnerable at a specific time – they are able to take advantage of that weakness.
- Longer duration – a real-world attack can take place over days, months, or even years, and because many types of attack vectors can take time to pay off (phishing, social engineering), a longer duration is usually required to provide realistic feedback.
- Parallel execution and fluid re-prioritization – there may be numerous different activities happening in parallel, and depending on the results of any given activity, the Red Team may decide to re-prioritize or change plans on the fly.
Read more about 15 smart strategies to ensure a successful red team exercise in this article from Forbes.
Let's Get Real
By embodying the thinking attacker viewpoint of a cybercriminal, each Red Team engagement helps to provide organizations with a much more realistic understanding of how they may really be attacked, and more importantly; where they may have weaknesses that make them vulnerable.
This information is critical to build even stronger defense strategies. In performing Red Team engagements for clients, Online has seen first-hand how these situations can end up shedding light on areas of security that may not have been identified by more traditional penetration testing in the past.
What can you Learn From a Red Team Engagement?
We recently performed a Red Team engagement for an organization that had an extensive and ongoing penetration testing program. Their program was targeted at protecting external and internal networks and applications.
The company also had its staff enlisted in phishing training exercises and was promoting a strong security awareness program.
However, much of the ongoing penetration testing program was executed with various limitations to the dates and times each test could be conducted, and with a scope limited to specific networks and applications at any given time.
Our Online Red Team, in contrast, was provided an extensive latitude to perform activities over a year-long period, perform attacks against any of the in-scope networks and applications, and allowed to perform social engineering attacks and physical site intrusions. This article from CrowdStrike contains an extensive list of the various types of social engineering attacks.
The number of people within the organization that was aware of our Red Team attack strategy was strictly limited to avoid putting users on the defensive.
The engagement helped this organization learn that all the network and application security controls that they had put in place, based on the information provided from previous penetration testing activities, was very effective.

The business also learned that while the users had been trained on phishing attacks, more training was required, as credential stealing attacks successfully exploited many of their employees. This seems to be the most common type of vulnerability as highlighted by Andrew Scott throughout his personal experiences. In addition, the organization's IT Security Team learned that their implementation of multi-factor authentication helped mitigate much of the risk of the successful credential gathering phishing attacks.
What the company was less aware of was the weaknesses identified in their physical security.
The Red Team targeted the Headquarters for this organization, which was a large facility employing a third-party, subcontracted, physical Security Team. The Red Team was able to get into the facility using several different methods and found many opportunities to connect rogue devices to their network.
The Online Red Teamers found office layouts and other incredibly useful information while inside the network. Gaining after-hours access to the physical security office, the Red Teamers were able to then access and print their own security badges, giving them full access to most of the facility.
The team determined that the organization did not properly limit external internet access. Therefore, the devices placed on the network were able to communicate outbound and provide ongoing access to the organization's internal network.
Online's Red Team used this position on the internal network to gain full network compromise. This blog from VaaData provides an excellent overview of how to secure internal networks.
Valuable real-world threats and vulnerabilities were exposed through this process.
Online’s Red Team Approach is a sophisticated 4 phase engagement that is customized to the specifics of each organization.
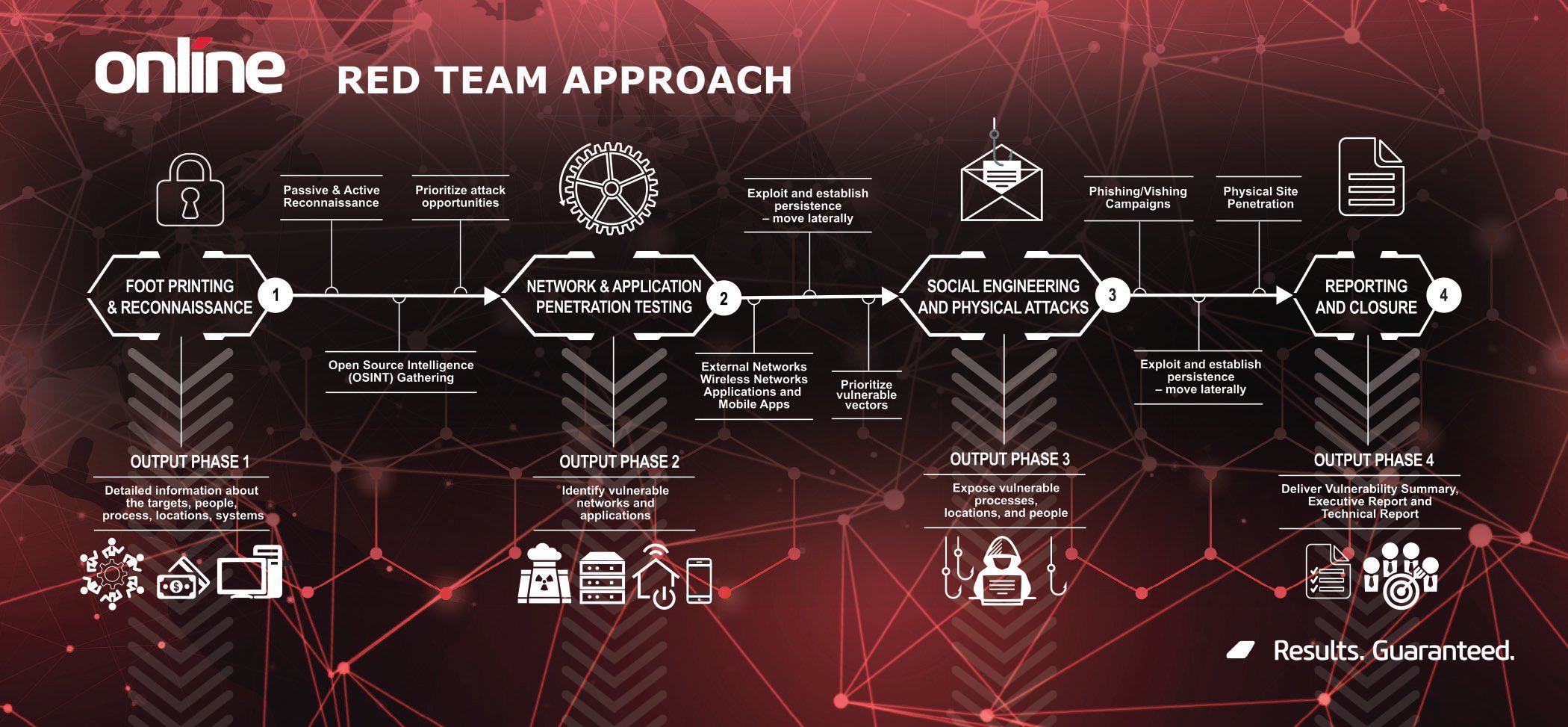 (Click here to download infographic)
(Click here to download infographic)
Red Team Results
The most important activity of the Red Team is not only the identification or exploitation of the weaknesses an organization might have. The critical takeaway is using this information to help an organization identify the most cost-effective solutions that lower the risk to an acceptable level. In this case, the organization had many healthy cybersecurity controls that were bypassed by some weaknesses in the security training of users (phishing), and a number of weaknesses in physical security.
By addressing the vulnerabilities – by focusing on specific training for employees and their subcontracted security vendor – the organization ensured that their investments in cybersecurity controls could not be circumvented by an attacker who is willing to utilize any number of different approaches to breach the target.
What's Ahead?
It is predicted throughout 2020 cybercrime will continue to grow at an exponential rate, led by hundreds of gangs who have deployed sophisticated targeted attacks on businesses large and small, and across all industries and consumer sectors. Advancement in AI technology and algorithms, facial and voice recognition software, bots and deepfakes are just a few of the new tools cybercriminals are using to bypass security measures and impose ransom. The International Data Corporation forecasts that cyber security spending will reach almost $200 billion in 2024 and security services will be the fastest growing market segment. Read more about the future of cyber security in this article.
It goes without saying, as the threat landscape changes, security measures must also continue to evolve.
The Red Team strategy is by far the most realistic, thorough and effective approach for exposing and preventing a breach. Deploying this thinking attacker styled method of testing could save your organization from having to realize the financial impact of an attack, whether it is a costly loss of intellectual property, ransom demand, downtime repercussions, or reputation repair.
Who will be the next target? That is an impossible question to answer.
Instead, ask yourself if your organization’s security testing is really identifying all the risks that it should. Book a Red Team consultation with us today.


.png)
.png)
Submit a Comment