Risk, Security & Privacy Team
A member of Online's EMEA Cybersecurity team recently shared today's piece as a LinkedIn post; we are pleased to share his thoughts on a very timely topic with you.
"As the war in Ukraine continues on the ground, a cyber-war is also taking place in the background. Various hacker groups including Anonymous and NB65 are very active.
Recently, NB65 was able to take over Russia's spy satellites and internet media declaring that "If we seem quiet, it's because we have an Olympic-sized swimming pool worth of data and vulnerabilities”.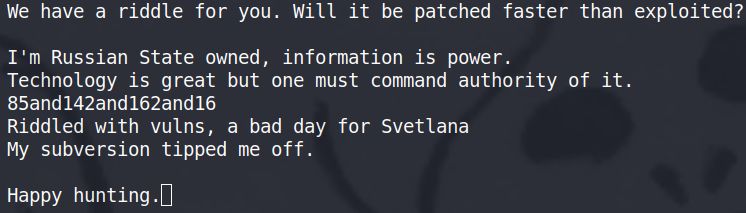
They are not boasting without merit – they have in fact identified numerous vulnerabilities and are slowly exploiting them.
This poses a few questions for us to consider:
1. Can we feel fully secure meeting ISO or PCI-DSS requirements in such a situation? We certainly can.
2. Have these standards taken into account the state of cyber-warfare? Certainly not.
3. Are we able to update our systems faster than vulnerabilities emerge? While I’ll leave this question unanswered, I will suggest that now is the time to go beyond the guidelines existing regulations and standards and do more to protect your assets and infrastructure.
Given the current situation, I strongly recommend the following additional measures:
1. More frequent external and internal vulnerability scans. My recommendation is once a week.
2. Extended logging for remote access to your Cardholder Data Environment (CDE).
3. Consider disabling or limiting remote access to a minimum number of authorized individuals.
4. Immediate forced password changes for users with access to CDE.
5. Expanded logging for category 2 devices.
6. Additional looking for and disabling of ineffective user accounts.
7. Weekly wi-fi reporting.
Whether your organization is based in Europe, North America, Africa, or elsewhere – now is the time to be extra cautious and extra vigilant."
*Republished with permission from the author
Organizations of all sizes need to understand their risk profile and ensure that they continually monitor their security posture. For some firms, this mandate falls to a full-time Chief Information Security Officer, for others, a Virtual CISO (vCISO) provides the most flexible approach to getting access to the needed expertise.
We invite you to watch this short video where James Devoy, our Managing Director, EMEA recalls concerns that were shared by his community back in the 1980s. These concerns, and the need to have a strong security leader in place, really resonate against the backdrop of present-day realities.




Submit a Comment