There has been a lot of discussion about the need to have an end-to-end plan to manage your security threats and vulnerabilities. It is easy to agree that our plans need to start at identification and continue through to remediation and we might quickly agree that the first step is to effectively identify the threats. What is far more difficult, is determining how these threats and vulnerabilities are identified; unfortunately, in the increasingly complex enterprise environments of today, this task can be incredibly difficult and in some cases, nearly impossible.
One of the biggest challenges organizations face in this ‘Identify’ stage today is identifying what potentially vulnerable assets they own. The pace of infrastructure growth plus the advent of advanced DevOps and complex hybrid cloud environments, has created such complexity that security and IT Operations professionals can’t keep track of what assets are in their environments. Business application architecture that used to change once or twice a year can now change weekly, daily, or even multiple times per day. Industry experts say that between 12% and 30% of IT assets in a large enterprise are untracked, unmanaged, and worse yet, unpatched to known vulnerabilities.
With the pace of change today, traditional methods such as manual inventories and home-grown tools can’t keep up and that means that asset inventories are never accurate. Worse yet, advanced DevOps and hybrid cloud environments mean that the dependency map of related assets is also in a constant state of flux. Tools such as the industry leading BMC Multi-Cloud Discovery are the only way that organizations can truly keep up with the pace of change and complexity.
Even when an organization has a near complete asset inventory, they are then faced with how to prioritize efforts to remediate threats and vulnerabilities. The myriad of threat detection and vulnerability scanning tools offer a tremendous volume of often conflicting information and none of it provides business context to the user. Security and IT Operations professionals can be faced with hundreds if not thousands of threats each day and in order to prioritize their scarce resources, they need to filter, correlate, and enrich the data with business context.
Advanced tools such as BMC Discovery, Flexera, and Apptio provide can provide Security and IT Operations professionals with not only accurate asset information, but an understanding of how their assets are interconnected, what their value is to the organization, and what business services they support. Patching a database server that supports your online banking system does you no good if you also have a serious vulnerability in the application server. Conversely, it makes no sense to devote significant effort to patching servers that are due to be decommissioned the following week.
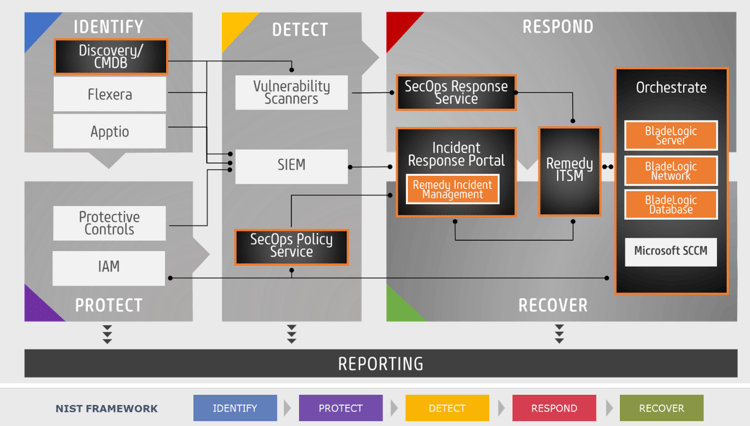
Online’s Security Integration Framework leverages advanced technology, strong process knowledge built around industry best practices, and the science of Organizational Change Management to help organizations tackle end to end threat and vulnerability management across all groups including Security and IT Operations. Our quick start assessment looks at all aspects of people, process, and technology in relation to your security challenges and provides quick win initiatives to improve your overall maturity.
Without exception, we have found that the number one quick win initiative is the implementation of an advanced automated discovery tool. This initiative can provide rapid improvement in the ability of Security and IT Operations to assess and prioritize their efforts to protect your assets. It can also greatly improve audit compliance, improve accuracy of the change management process and reduce overall operations costs substantially.
To learn more about Online’s Security Integration Framework and our approach to implementing automated discovery, please visit our Security Integration Framework Resource Center or leave a comment below.





Submit a Comment