A note from the author: As I talk to more and more organizations a new challenge is emerging: balancing the need to be secure and the need have systems operational. I’ve written this blog post from an internal perspective (CEO) to provide an “insider” view on the problem. While not meant to describe operations at any firm specifically, the challenges identified and the solutions required to resolve them are real and attainable with the right team and the right skills.
In Part One of my blog, I described the challenges our organization is facing due to the “Sec Ops Gap” between our IT Operations and Security Operations teams. We discovered that the two team’s goals and objectives are not aligned and we realized that the metrics they use for performance are often in conflict with each other. Processes are not integrated end-to-end, causing huge inefficiencies and making compliance impossible to report. Technologies are also not integrated and critical data is not being shared.
Now let’s look at how our organization has started to bridge this gap.
At the outset, we believed that technology alone would not solve the problem. In fact, we believed that if we attempted to implement a technological solution before we got our house in order, it would likely exacerbated the problem rather than resolve it. Recent research from Gartner[1] echoed our belief that People and Processes were critical pre-requisites to closing the technology gap. We felt like we were on the right track when we saw that the top six concerns cited in a survey of 353 IT executives have nothing to do with a technology solution:
- A shortage of people and skills to successfully implement IT automation
- A lack of documentation of existing processes
- A cultural resistance inside the Infrastructure & Operations team
- A lack of process, standards, and standardization expertise
- Low infrastructure and operations maturity
- No clear business case
- Consolidation of automation tools
We could not tackle everything at once. To build our roadmap we used an assessment tool to measure our current state alignment of three dimensions of the Sec Ops gap: People, Processes, and Technologies. We started with a baseline assessment of our security controls using the NIST Cybersecurity Framework (CSF), a widely-accepted security control classification scheme as a frame of reference. We also completed a baseline IT Operations process assessment using the ITIL framework. These two assessments, completed in a handful of days, enabled us to identify “hot spots” to focus on, resulting in some quick wins that allowed us to make progress early on.
Next we assessed the three dimensions of the Sec Ops gap and examined high priority/high risk processes from an inventory of sixty security processes that require Security Operations and IT Operations to be closely integrated. We asked ourselves the following questions:
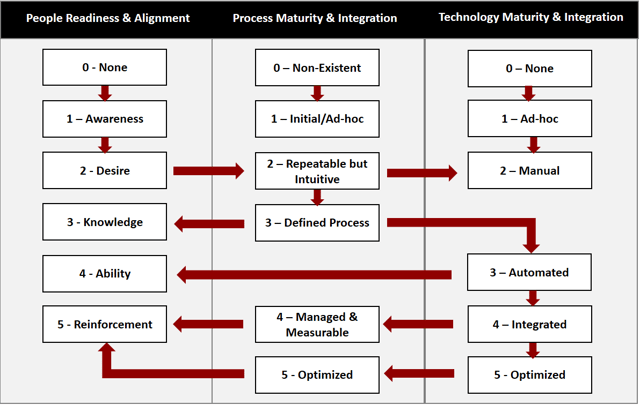
People Readiness for Change and Alignment: Is there awareness of the redundancies and overlapping work? What about awareness around the business benefit of a single, shared process? Have business objectives been articulated that generate a desire to change? Is there a single process owner from end-to-end? Do the teams speak the same language and do they have the knowledge and ability to execute the process? Are the teams’ performances reinforced using common metrics and KPIs?
Process Maturity and Integration: Does any process documentation exist, or is this an area we need to improve on? Are there shared, standardized processes? Or are they redundant, non-integrated activities that are hanging together due to culture alone? Do we have a defined, documented process with clear procedures, roles, and responsibilities? Do we monitor and measure compliance with standards, and do our metrics reflect this? Do we use performance data to continuously optimize our process?
Technology Maturity and Integration. Are we sharing data between the two teams? Do we use more than spreadsheets? Is there an identified “book of record” for key data sources used by both teams, and is it referenced when needed? Have we automated the workflow required to implement the process, from end-to-end? Do the teams use a shared system which supports separation of duties yet allows them to collaborate as required? Does it collect the metrics we need to manage and optimize our processes?
We identified target state maturity levels for each process area and, using gaps from current state, prioritized our improvement initiatives for People Alignment, Process Maturity/Integration, and Technology Maturity/Integration to achieve the greatest overall business risk reduction. It was clear to us that we needed to address the People dimension first and could not improve our Process Maturity until we had reached sufficient maturity on our People scale. Likewise, we could not improve our Technology maturity significantly until we had matured our Processes to at least a “Defined” level.
Benefits
We have followed the above approach, tackling processes incrementally each quarter, and it has yielded the following benefits for what we have completed so far:
|
Before |
After |
|
Processes are not integrated, and in many cases also not defined. |
Processes are defined and integrated. We are not 100% complete yet, but are tackling them in priority/risk order. |
|
Data exchange is ad hoc and manual, using little more than spreadsheets to record data. |
Systems of record are defined and data is shared across the two teams. |
|
We cannot validate what has been addressed and what hasn’t. |
We have end-to-end workflows and we know exactly what has been addressed and what hasn’t yet. |
|
We cannot optimize the use of scarce resources to minimize overall risk to the enterprise. |
We apply resources to the highest risk threats, identified using a combination of threat, exploitability, business impact and business context data, to minimize the risk to the business. |
|
We don’t have the data we need to make business-driven security decisions to maximize the value of our efforts. |
|
|
Our compliance group cannot confidently report compliance to our auditors/regulators. |
The compliance data we report is a natural by-product of our end-to-end process and technology integration. |
|
Even some known threats don’t get addressed. We do not know what risk this poses. |
Known threats are tracked and addressed in priority order. Mitigating controls are considered when a threat cannot be remediated quickly enough. Our overall risk is known and quantifiable at any point. |
|
Ownership of these problems and the resolution is murky. |
Ownership of security is clearly a joint responsibility. Our teams are measured using shared security and business risk KPI’s. We have champions responsible for measuring and improving each of our security processes. |
We continue to evolve and improve. It has taken a unique combination of skills in cybersecurity, IT Operations, and Organizational Change Management for us to be successful. Maintaining our security posture is a continuous journey, but we have a proven and mature approach guiding us to maximize the benefits and minimize the risks to our business.
As a TOGAF and ITIL-certified Enterprise Architect in our Risk, Security and Privacy practice, I understand the ‘big picture’ view of the challenges that organizations are facing.
To continue the conversation, feel free to leave a comment below. You can also learn more about Online's Service Management and Risk, Security and Privacy practices here.
[1] How to Avoid the Five Most-Common IT Automation Pitfalls, Gartner, December 2015




Submit a Comment