A note from the author: As I talk to more and more organizations a new challenge is emerging: balancing the need to be secure with the need to have operational systems. I’ve written this blog post from an internal perspective (CEO) to provide an “insider” view on the problem. While not meant to describe operations at any firm specifically, the challenges identified and the solutions required to resolve them are real and attainable with the right team and the right skills.
Our business is at risk. The number of security threats to our IT assets - our information,
systems, devices, facilities, and personnel - continues to rise, but our approach to dealing with them is not yet mature enough to adequately mitigate the associated risk.
Though we can quantify the level of risk that individual threats pose to our environment, we cannot quantify the overall aggregate risk to our business, which means we also can’t optimize our response to that risk, monitor the reduction of that risk over time, or confidently report on it.
Our regulators, clients, business partners, and industries require us to demonstrate we are properly addressing risk by putting appropriate safeguards in place, but we do not have the integrated systems and data required to prove ongoing compliance.
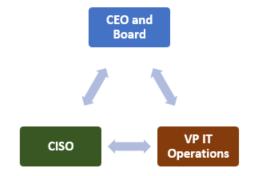
Our VP of Operations and his team are measured on their ability to maintain uptime, availability, and performance, while our CISO and her team are measured on their ability to address vulnerabilities and threats to keep our IT assets safe. These can be conflicting objectives.
There is a breakdown in aligning priorities between the board and Security Operations. A communications gap (Sec Ops Gap[1]) exists where our IT Operations and Security don’t understand each other’s concerns and priorities, and perhaps more concerning is that their success is measured based on achieving – at times - conflicting objectives. Our current reality is that:
- Processes are not integrated, and in many cases also not defined.
- Data exchange is ad hoc and manual, using little more than spreadsheets to record data.
- We cannot validate what has been addressed and what hasn’t.
- We cannot optimize the use of scarce resources to minimize overall risk to the enterprise.
- We don’t have the data we need to make business-driven security decisions to maximize the value of our efforts.
- Our compliance group cannot confidently report compliance to our regulators.
- Even some known threats don’t get addressed. We do not know what risk this poses.
- Ownership of these problems and the resolution is murky.
As CEO, I know that closing these gaps is critical. If we applied a maturity model to assess our current practices we would be at “Level 1 - Initial/Ad hoc”, or “Level 2 – Repeatable but Intuitive”, at best. This is not good enough to safeguard our business or satisfy our regulators, clients, or business partners. We need to apply the same rigor we apply to other mission critical processes to this Sec Ops gap.
As I think about the future and translate where we need to be against the COBIT maturity model I can see many benefits at each stage:
Level 2 - Repeatable but Intuitive
- IT Ops and Sec Ops understand how to work together and communicate frequently.
- Processes are understood and similar procedures are followed by different people undertaking the same task.
Level 3 - Defined Process
- Processes are formally documented and span the Sec Ops gap.
- Ownership of problems and resolution is clear.
- Procedures are standardized, documented, and communicated through training.
- Our processes generate the data required for accurate compliance reporting.
Level 4 - Managed and Measurable
- Service level targets are defined and clearly understood.
- We monitor service levels and escalate issues as required.
- Security Operations and IT Operations are measured using shared metrics and KPI’s.
Level 5 - Optimized
- We use IT resources efficiently and make risk mitigation decisions that take into account the threat and quantified risk, characteristics of the asset, and business context and impact.
- We measure and monitor the overall risk to the enterprise.
- What we learn is captured to provide feedback into the ongoing process.
Now how will we get to this state of maturity? In my next blog I will discuss how we plan to move upwards through these maturity levels, and how a company like Online Business Systems may be the key to our success.
As a TOGAF and ITIL-certified Enterprise Architect in our Risk, Security and Privacy practice, I understand the ‘big picture’ view of the challenge that organizations are facing. To continue the conversation, feel free to leave a comment below.
You can also learn more about Online’s Service Management and Risk, Security and Privacy practices here.
[1] Forbes Insights term. http://www.forbes.com/forbesinsights/bmc/index.html




Submit a Comment